What is AssetView?
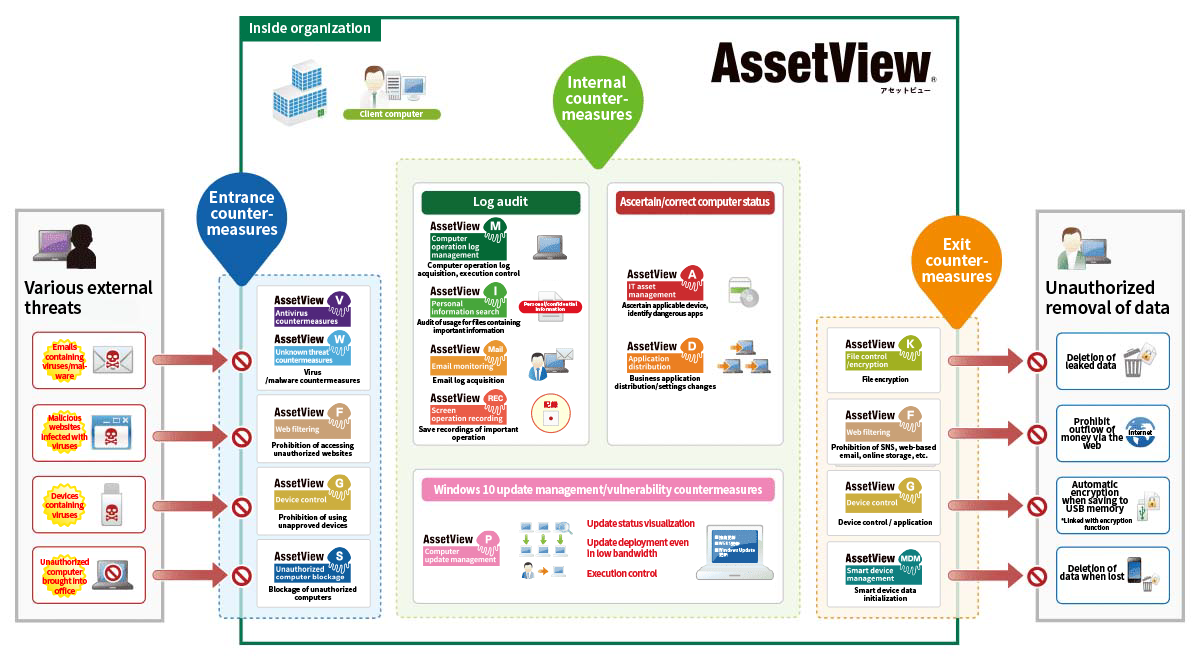
AssetView is comprehensive IT security for protecting the customer’s organization and information. In recent years, threats continue to increase and cyberattacks are becoming more diversified. Therefore, it is essential to implement security measures for the endpoints which are corporate IT assets. In particular, measures against information leakage must be comprehensively managed from many different angles. At the same time, in order to minimize the cost of introducing IT security measures, it is also important to select and implement the functions required for the customer's environment. With AssetView, users can select such functions and reduce the burden on those in charge of corporate information systems. This reduces system introduction costs and improves operational efficiency.
Features
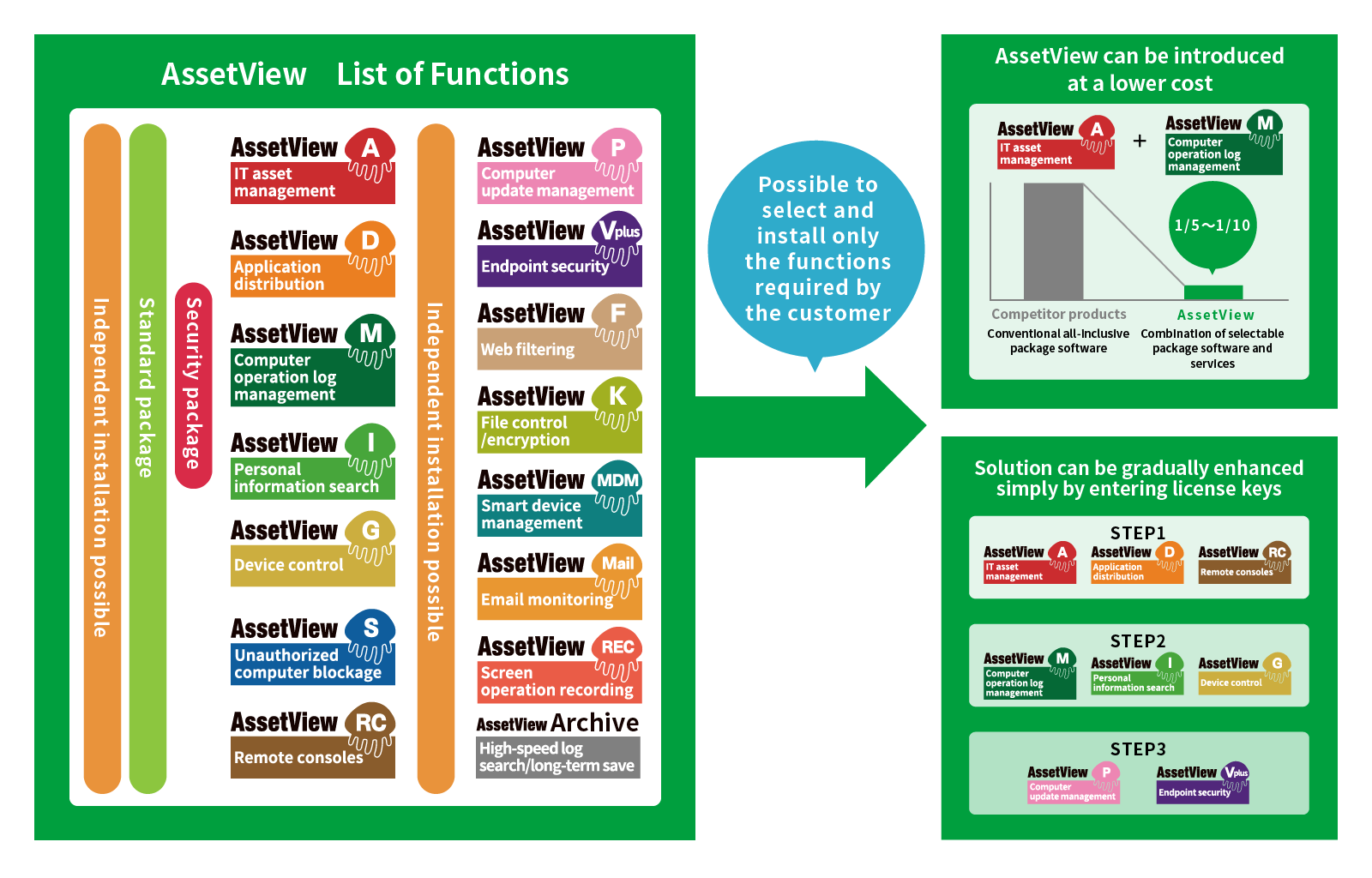
- Introduction is possible from a single function to custom-made selection of multiple functions
- 15 types of functions can be added after introduction
- Achieves maximum efficiency at minimum cost
- Supports planning and phased introduction through each step according to the situation of asset management at the customer
- Offers intuitive operation similar to a web browser, and efficient extraction/correction of information similar to Excel
- Enables gradual introduction of functions
- Also enables flexible addition of licenses
- Cloud service is available in addition to on premise service
The service will solve problems such as the following:
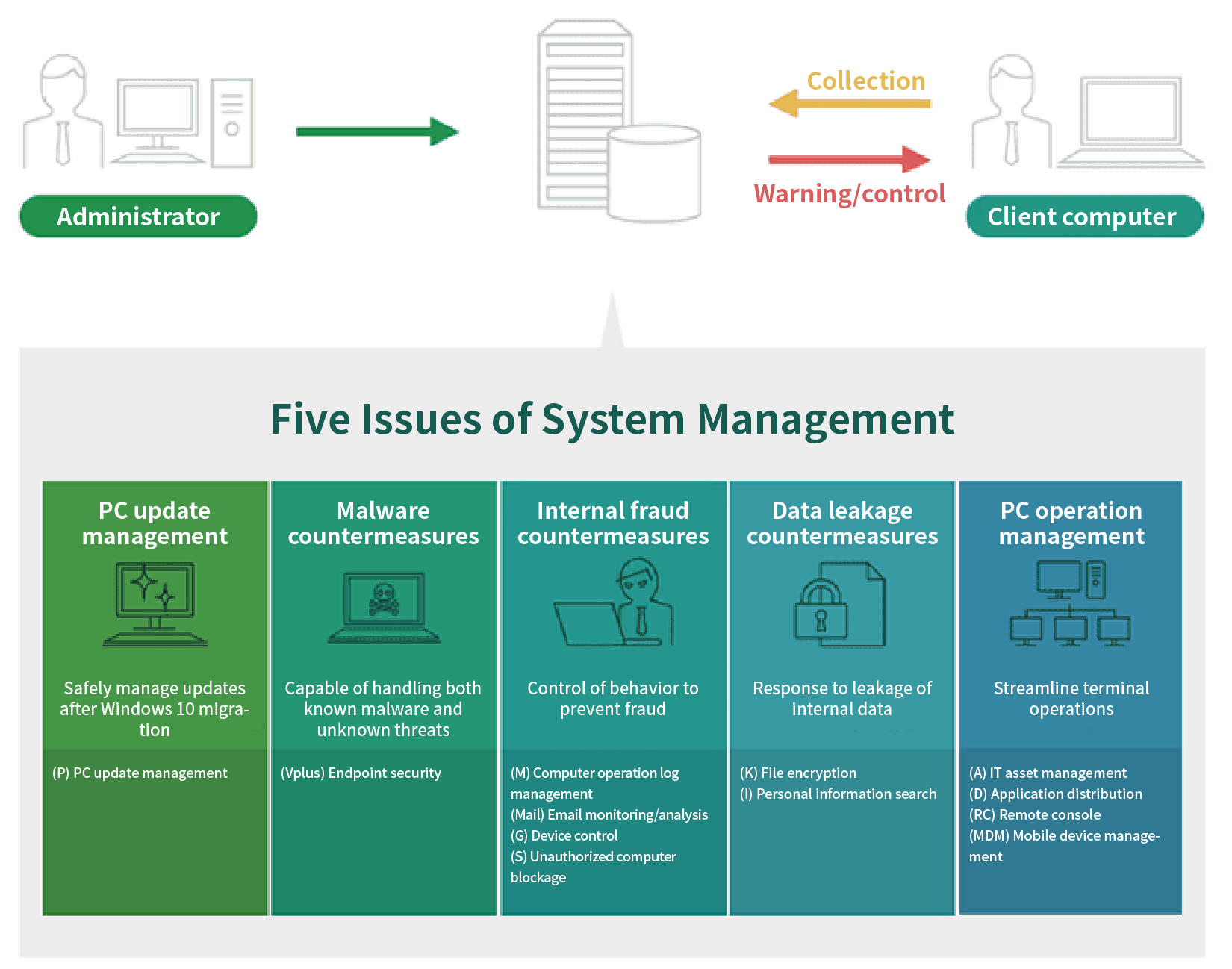
- Want to efficiently and easily manage assets
- Want to safely manage updates after migrating to Windows 10
- Want to prevent infection by new viruses
- Want to respond to leakage of internal data
- Want to monitor and control employee behavior during work
- Want to restrict access to prohibited sites, SNS, etc.
Main Functions
| On-premise | Cloud | |
|---|---|---|
 |
|
|
 |
|
|
 |
|
|
 |
|
|
 |
|
|
 |
|
|
 |
|
|
 |
|
|
 |
|
|
 |
|
|
 |
|
|
 |
|
|
 |
|
|
 |
|
- |
 |
|
- |
 |
|
- |