What is Azure Defender for IoT?
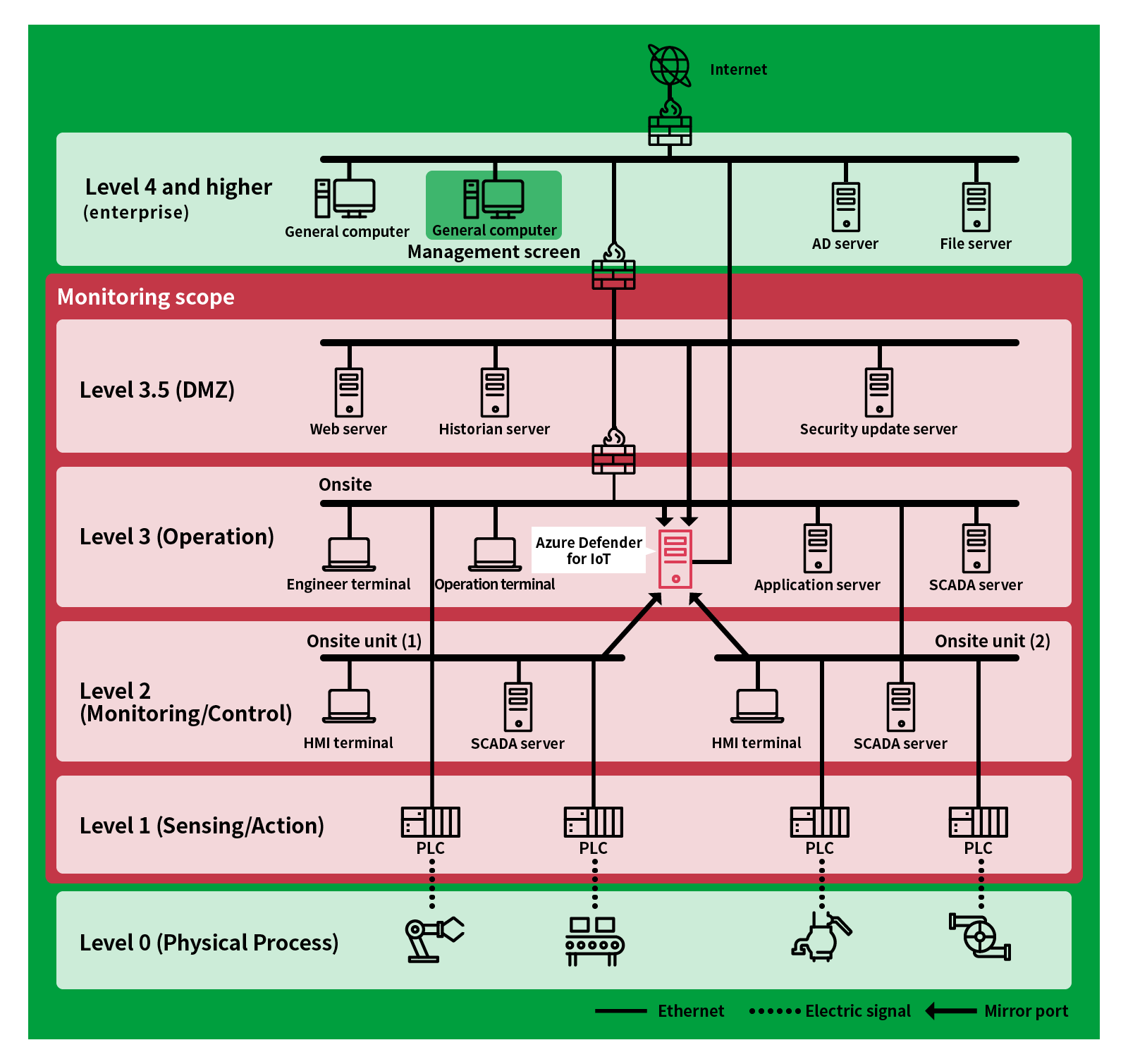
Azure Defender for IoT is provided as a security solution specialized for OT (Operational Technology) environments and ICS.
This cybersecurity solution for ICS was researched and developed by a former Israel Defense Force security expert. Furthermore, an SDK has been introduced for Azure Defender for IoT. This provides support for Japan’s unique private protocol, something which had been difficult until now. It is also possible to add fast protocol support, Japanese translations of alerts, and arbitrary messaging.
Features
- Specialized design for OT (Operational Technology)
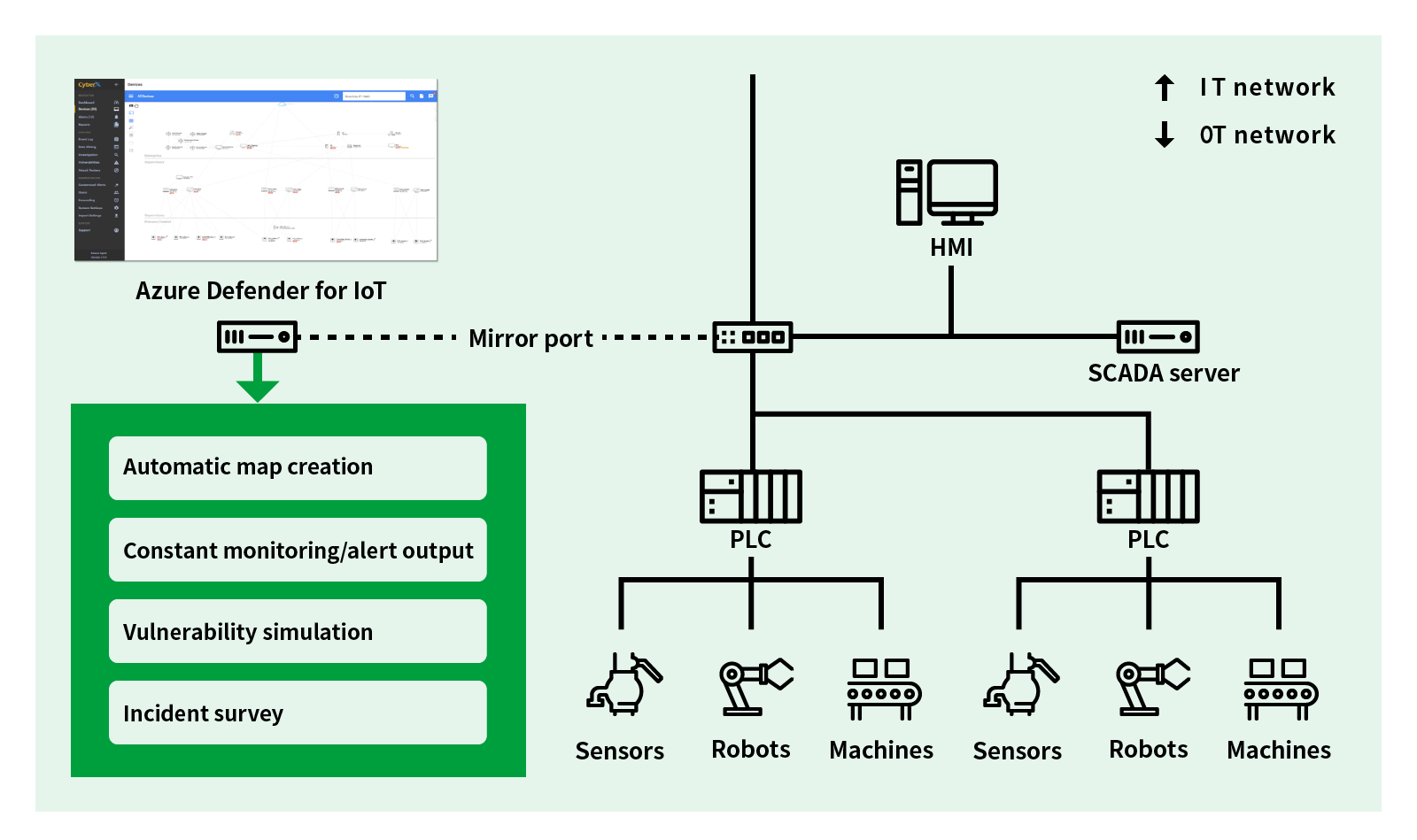
Azure Defender for IoT utilizes a unique M2M (Machine to Machine) technology behavior analysis algorithm and ICS-specific threat intelligence. Special industrial protocols are supported, so the solution constantly monitors the customer’s OT environment and quickly detects the occurrence of incidents. - No impact on existing networks
Since packet acquisition consists of only one-way communication from the mirror port, there is no need to worry about problems such as existing industrial equipment being shut down. - Implementation of function for predicting attack vector
By evaluating vulnerabilities in all the customer’ assets, the solution is able to predict attack vectors when used in combination. This makes it possible to determine which devices should be prioritized for security measures.
The service addresses areas including:
- Continuously monitoring OT environments, evaluating risks, and formulating effective measures.
- Taking prompt and proactive responses to serious vulnerabilities.
- Evaluating and diagnosing devices in an OT environment and analyzing vulnerability information.
Main Functions
Vulnerability assessment
Azure Defender for IoT can comprehensively assign scores based on the number of detected vulnerabilities, the number of devices, etc., and output an assessment report for clearly grasping the required security measures.
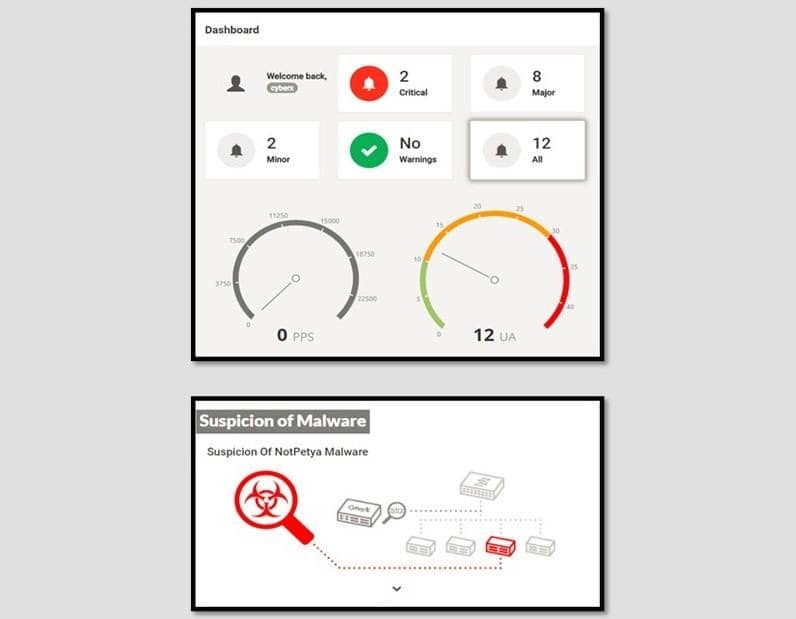
Constant monitoring/real-time alerts
Azure Defender for IoT uses machine learning to create a network baseline, and to automatically evaluate vulnerabilities and risks that do not impact the existing environment. Furthermore, the solution is equipped with five types of control engines for immediate detection of abnormal behavior.
- Detection of protocol violations
- Detection of policy violations
- Detection of malware
- Detection of abnormalities
- Detection of operation changes
Display event log
Display alert-related events in an easy-to-view timeline format.
Alert report
Alert-related reports can be downloaded in a PDF format.
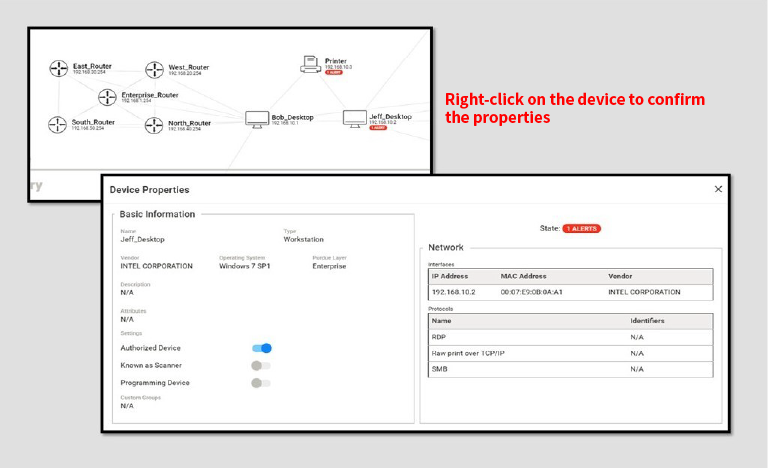
Automatic creation of network topology
Simply connect to the network and it will automatically create a map of the assets connected to the same network.
Display asset properties
Together with the map, it automatically creates asset properties connected to a network.
Report function
A large number of reports (approx. 20 types) can be used.
Data mining function
Users themselves can also create (mining) forms that are not provided in the report.
Predict attack vector
Based on vulnerability information for each asset, Azure Defender for IoT predicts the attack vector that may be a cyberattack.
Security measures simulation
Creates a simulation assuming that security measures were taken based on the predicted attack vector.
Centralized management console
Even in large-scale environments, integrated management is possible using the centralized management console.
SIEM linkage
By linking with the API, it is possible to merge it with the main SIEM.
Vulnerability assessment
Azure Defender for IoT can comprehensively assign scores based on the number of detected vulnerabilities, the number of devices, etc.,and output an assessment report for clearly grasping the required security measures.

Constant monitoring/real-time alerts
Azure Defender for IoT uses machine learning to create a network baseline, and to automatically evaluate vulnerabilities and risks that do not impact the existing environment. Furthermore, the solution is equipped with five types of control engines for immediate detection of abnormal behavior.
- Detection of protocol violation
- Detection of policy violations
- Detection of malware
- Detection of abnormalities
- Detection of operation changes
Display event log
Display alert-related events in an easy-to-view timeline.
Alert report
Alert-related reports can be downloaded in a PDF format.
Automatic creation of network topology
Simply connect to the network and it will automatically create a map of assets connected to the same network.
Display asset properties
Together with the map, automatically creates the properties of assets connected to a network.
Report function
A large number of reports (approx. 20 types) can be used.
Data mining function
Users themselves can also create (mining) forms that are not provided in the report.
Predict attack vector
Based on vulnerability information for each asset, Azure Defender for IoT predicts the attack vector that may be a cyberattack.
Security measures simulation
Creates a simulation assuming that security measures were taken based on the predicted attack vector.
Centralized management console
Even in large-scale environments, integrated management is possible using the centralized management console.
SIEM linkage
By linking with API, it is possible to merge with the main SIEM.
Price
Please contact us for details.
Specifications
Hardware appliance
[1U Model: HPE ProLiant DL20]

| CPU | Intel Xeon E-2224, 3.4GHz,4C,71W |
| Memory | 1x8GB Dual Rank x8 DDR4-2666 |
| Storage | 2 x 1TB SATA 6G Midline 7.2K SFF (2.5in) – RAID 1 with Smart Array P208i-a |
| Network controller | On-board: 2 x 1Gb On-board: iLO Port Card 1Gb External: 1 x HPE Ethernet 1Gb 4-port 366FLR Adapter |
| Power source | Dual Hot Plug Power Supplies 350W |
| Max Protected Devices | 1,000 (*differs depending on environment) |
[Highly-Durable Model: Neousys Nuvo-7006LP/3Y]

| CPU | Core i5-6500TE 2.30GHz 6MB 4C/4T |
| Memory | DDR4-2666 non-ECC SO-DIMM 8GB |
| Storage | 2.5インチ SATA SSD MLC 128GB Temperature expansion products |
| Network controller | Intel i219 + i210 1GbE RJ45 6 ports |
| Power source | 120W AC/DC adaptor |
| Max Protected Devices | 200 (*differs depending on environment) |