What is the Targeted Attack Email Training Service?
The Targeted Attack Email Training Service is a solution for dealing with targeted attack emails. These are a form of advanced and sophisticated cyberattacks that specifically target a corporation or organization.
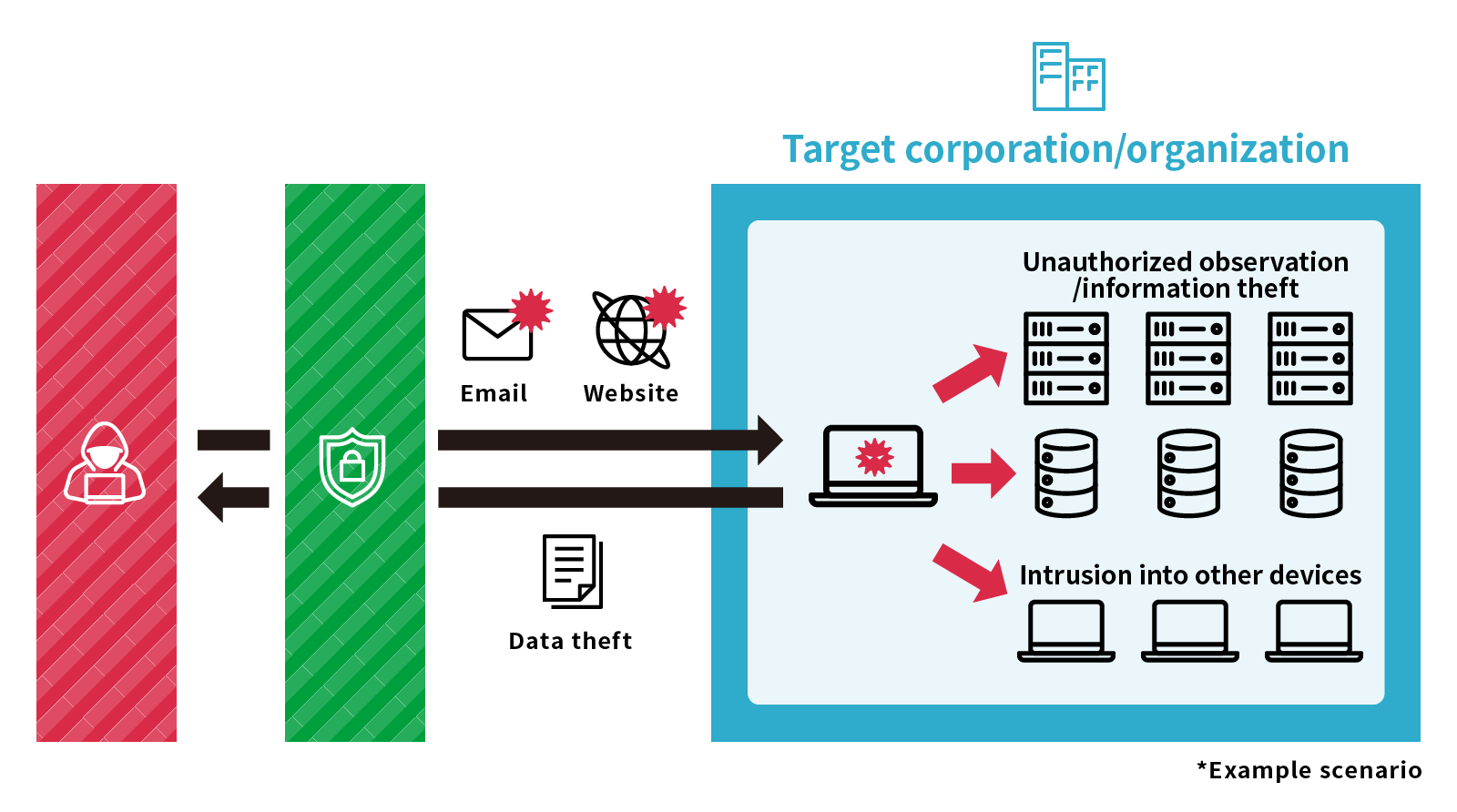
The attacker starts by collecting information about the target corporation, organization, and affiliated employees. Then, they impersonate employees, related organizations, or outside parties through making inquiries and using various methods to send emails containing malware. If even one computer in an organization becomes infected with malware, the attacker is able to collect information from others on the same network. The attacker then uses the gathered information to access servers and databases in the organization, or to continuously spread malware to other computers with the goal of gaining unauthorized access to more machines. In the event that important administrator authority, etc., is stolen and device control authority within the organization is taken by an attacker, it is possible that they will continue to conduct unauthorized observation of the organization and to exploit information.
The Targeted Attack Email Training Service trains personnel to understand important points for identifying suspicious emails and internal reporting flow. This will prepare companies in the case that they receive an actually targeted attack email. Holding continuous training will reduce the risk of unauthorized access to internal systems by targeted attacks, and will raise the security awareness.
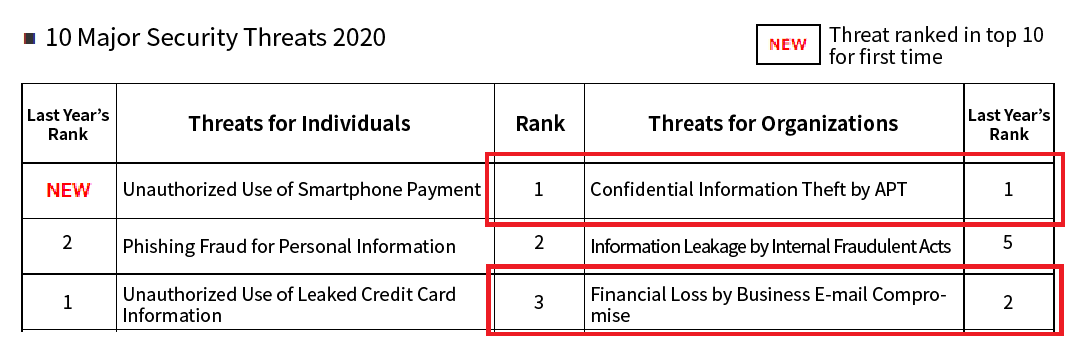
In IPA’s “10 Major Security Threats 2020,” the top threat to companies and organizations was “Confidential Information Theft by APT (Advanced Persistent Threats),” and the third-ranked threat was “Financial Loss by Business E-mail Compromise.”
Source: 10 Major Security Threats 2020 (IPA)
https://www.ipa.go.jp/security/vuln/10threats2020.html
Additionally, the Cybersecurity Management Guidelines also describe “targeted attack email training” and recommend that corporations hold training for their employees.
Source: Cybersecurity Management Guidelines 2.0 (Ministry of Economy, Trade and Industry)
https://www.meti.go.jp/press/2017/11/20171116003/20171116003-1.pdf
Features
- A pseudo targeted attack email is sent to the user for training purposes. If the user opens an attached file or link, the pseudo attack is revealed in the training site. By notifying the user of the risk and conducting a follow-up questionnaire, the drill raises the security awareness of employees.
- Educational courses can be held by security specialists during and after the training.
- Log aggregation and training implementation reports based on the results of the questionnaire are also provided. This information can be used for future security measures.
- The service can be customized according to the customer’s environment and situation.
The service will solve problems such as the following.
- I am unable to identify suspicious emails.
- I don’t know the initial response to be taken when attacked. Or, I want to confirm the capability of responding according to rules.
- I want to raise awareness toward targeted attack emails and other forms of cyberattacks.
Main Services
- A pseudo targeted attack email is sent to the specified email addresses. The status of opening URL links and attachments by recipients is aggregated.
- Security awareness is heightened by creating awareness of risks and conducting a follow-up survey.
- Educational courses are held by security specialists (optional).
- Log collection results and training implementation reports are provided based on questionnaire results.
- We are capable of customized proposals to fit the customer’s needs and budget.
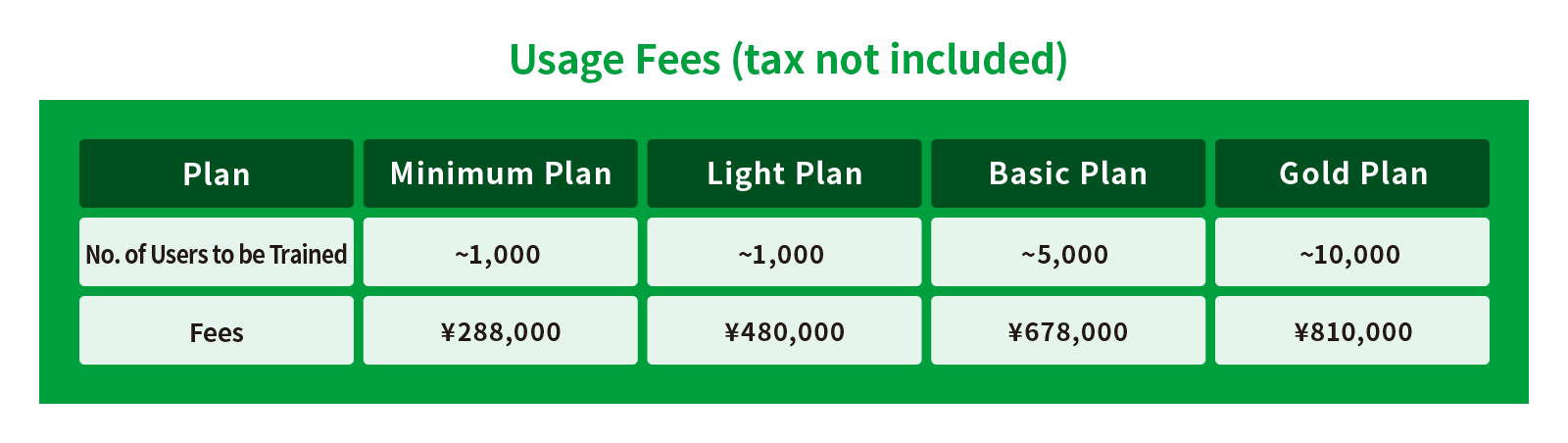
Price
Please feel free to contact us to receive a quote for each service.