What is MVISION Endpoint / EDR?
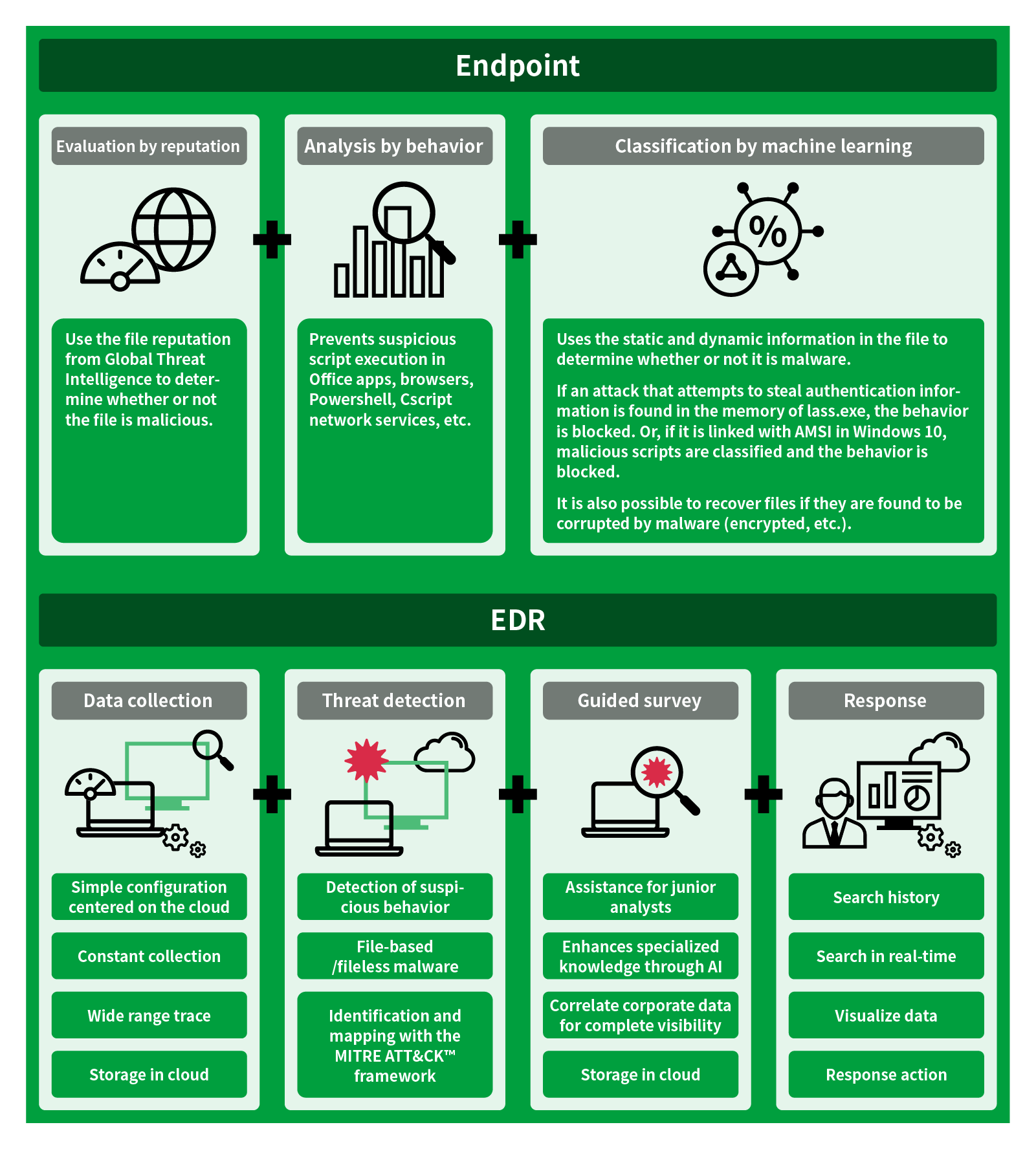
MVISION Endpoint / EDR supports customer endpoint security by simplifying powerful threat detection, investigation, and response. The EDR combines cloud-based SaaS management services and next-generation anti-virus measures with the high-level expanded protection function of Windows 10, and cloud native data and application security among SaaS, IaaS, and PaaS. Furthermore, endpoints such as iOS and Android terminals can be centrally managed, and protection for mobile devices is also possible. This makes MVISION Endpoint / EDR optimal for telework and mobile business applications.
Features
- Provides a simple cloud-based SaaS management service
- Windows 10 expanded protection function capable of integrated management
- Cloud native data and application security among SaaS, IaaS, and PaaS
- Simplifies threat detection, investigation, and response
- Centralized management and protection of iOS and Android
- Enhances specialized knowledge through AI
The service will solve problems such as:
- It is difficult for analysts to respond quickly to security operations
- In many cases, it is not possible to prove whether or not accurate judgment was made
- Investigations taking a long time
- Wanting to increase the efficiency of security and incident response
Main Functions
Monitoring
- Isolates terminals; stops and deletes processes
- Displays alarm on client at time of network isolation
- Displays the behavior of detected threats (visualizes the movement of threats)
- Visualizes threat information
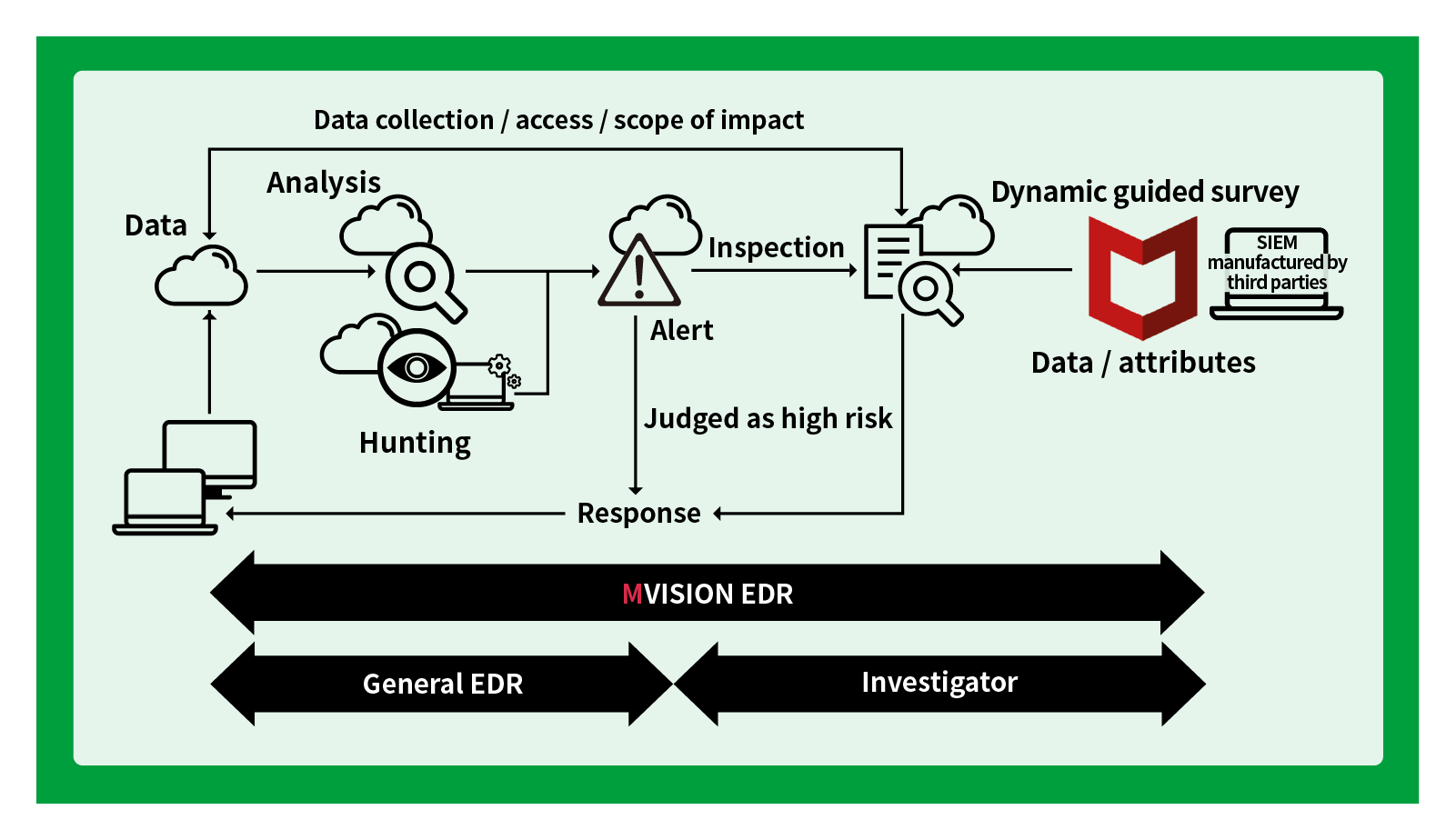
Investigating
- Analytical approach that automatically draws conclusions from hypothesis/confirmation methods
- Increases efficiency of device status
- Incident analysis and management of each case from snapshots of terminals
- Visualizes the analysis results of snapshots
- Emphasizes the display of specific entities
Historical Search
- Saves terminal trace data to the cloud (when an incident occurs, investigation is possible even when offline)
- By searching historical logs, it is possible to ascertain what happened before and after the malware infection
Real-time Search
- Real-time search of terminals