What is the Cybersecurity Assessment and Roadmap Formulation Service?
Based on an understanding of the customer’s thoughts and feelings, and on our mission , ID performs all necessary tasks from risk assessment to roadmap formulation in order to protect the customer from cybersecurity risks. We also provide services for control system environments, an area which has been attracting attention in recent years.
Features
Risk assessment
- Analyze the status of a customer environment based on internal policies, products used, and the operational status of those policies/products
- Conduct an investigation to determine what security risks are present
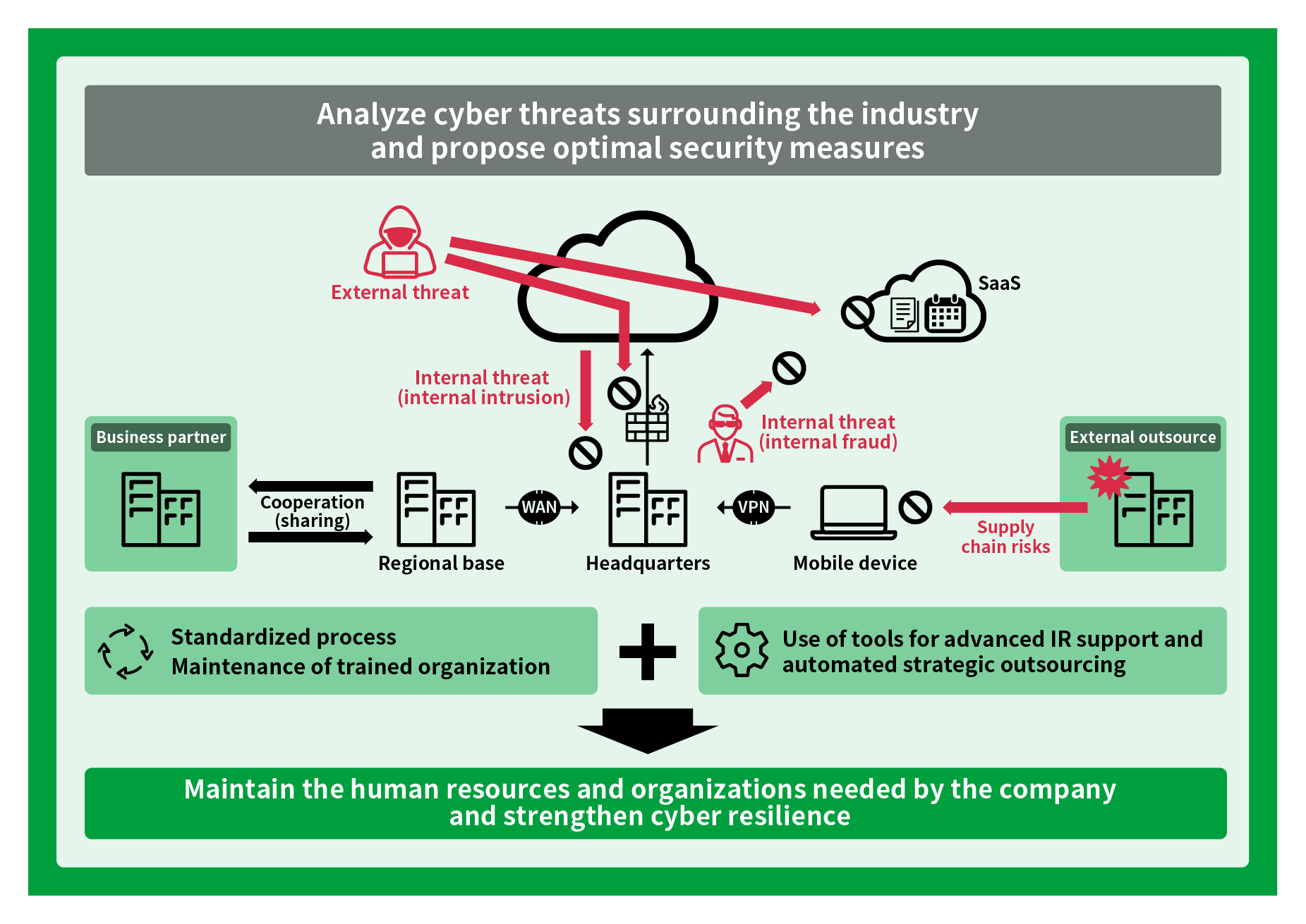
Present the direction of measures
- Analyze cyber threats surrounding the industry and propose optimal security measures for customers
Roadmap formulation
- Create a roadmap for implementing security measures, while considering the degree of priority according to the customer's environment
The service will solve problems such as the following.
- I want specialists to devise cyber security tailored to my company.
- I want to constantly implement the latest cybersecurity.
- I don’t understand what kind of threat is posed by a cyber-threat.
- I would like a specialist review my company’s current environment.
Main Services
[Example of risk assessment]
| Item no. | Check item | Check item details | Confirmation results |
|---|---|---|---|
| 1 | Region where the data center is located (country, state, etc.) | You can only select domestic locations, including for backup. | Data centers are scattered throughout Europe, the Americas, and Asia. You can select the data storage location, but cannot select a domestic location. |
| 2 | Governing law and court of jurisdiction in the event of a dispute | Confirm the governing law and court of jurisdiction in the event of a dispute. (Ministry of Economy, Trade and Industry Guidelines “15.1.1 Identification of Applicable Laws”) |
Disputes shall be resolved in compliance with XXXX state law. Service provision contract Governing law. Legal proceedings may be taken only in courts located in the state of XX in accordance with the laws of the state of XX (excluding the provisions of conflict of laws) for any claims arising out of or related to this contract or this service. Both parties agree to in person jurisdiction of these courts. |
| 3 | Data encryption User management of encryption key |
It is possible to implement a function that encrypts data on a cloud service and enables management of the encryption key by the user, not the cloud operator. (Ministry of Economy, Trade and Industry Guidelines “12.3.2 Key Management”) |
It does not provide a function for data encryption on the user side. |
| 4 | Authentication method for administrator web interface (Multi-factor authentication, password management) |
An expiration date is set for the password. Multi-factor authentication is being used. |
An expiration date is not set for the password. *Using two-factor authentication function will minimize the possibility of unauthorized login. |
| 5 | Feasibility of conducting audits | Capable of accepting audit requests from cloud users. | The description related to acceptance of audit requests from cloud users cannot be confirmed from public information. |
[Roadmap example]
| No. | Measures | Year 1 | Year 2 | Year 3 | |||
|---|---|---|---|---|---|---|---|
| 1Q | 2Q | 3Q | 4Q | ||||
| 1 | Process standardization Monitoring |
Updating of business system regulations, etc. Creation of new related regulations |
Revision of rules | Revision of rules | |||
| 2 | Asset inventory and classification Risk analysis |
Risk analysis | Risk analysis | ||||
| 3 | Risk assessment of cloud service | Cloud service required items Creation of guidelines |
Cloud evaluation | Cloud vulnerability diagnosis | Cloud evaluation | ||
| 4 | Expanded scope of vulnerability diagnosis | Platform diagnosis | Web application platform diagnosis | Web application/platform diagnosis | Web application/platform diagnosis | ||
| 5 | Strengthened incident response capability (technical) | Endpoint detection/defense effect | Advisory service | ||||
| Strengthening of server detection/defense | Setting of definitions for log analysis | Setting of definitions for log analysis | |||||
| 6 | Strengthened incident response capability (personnel) | Security education | Incident training Targeted email training |
Security educationIncident training Email training |
Security educationIncident training Email training |
||