What is Seceon?
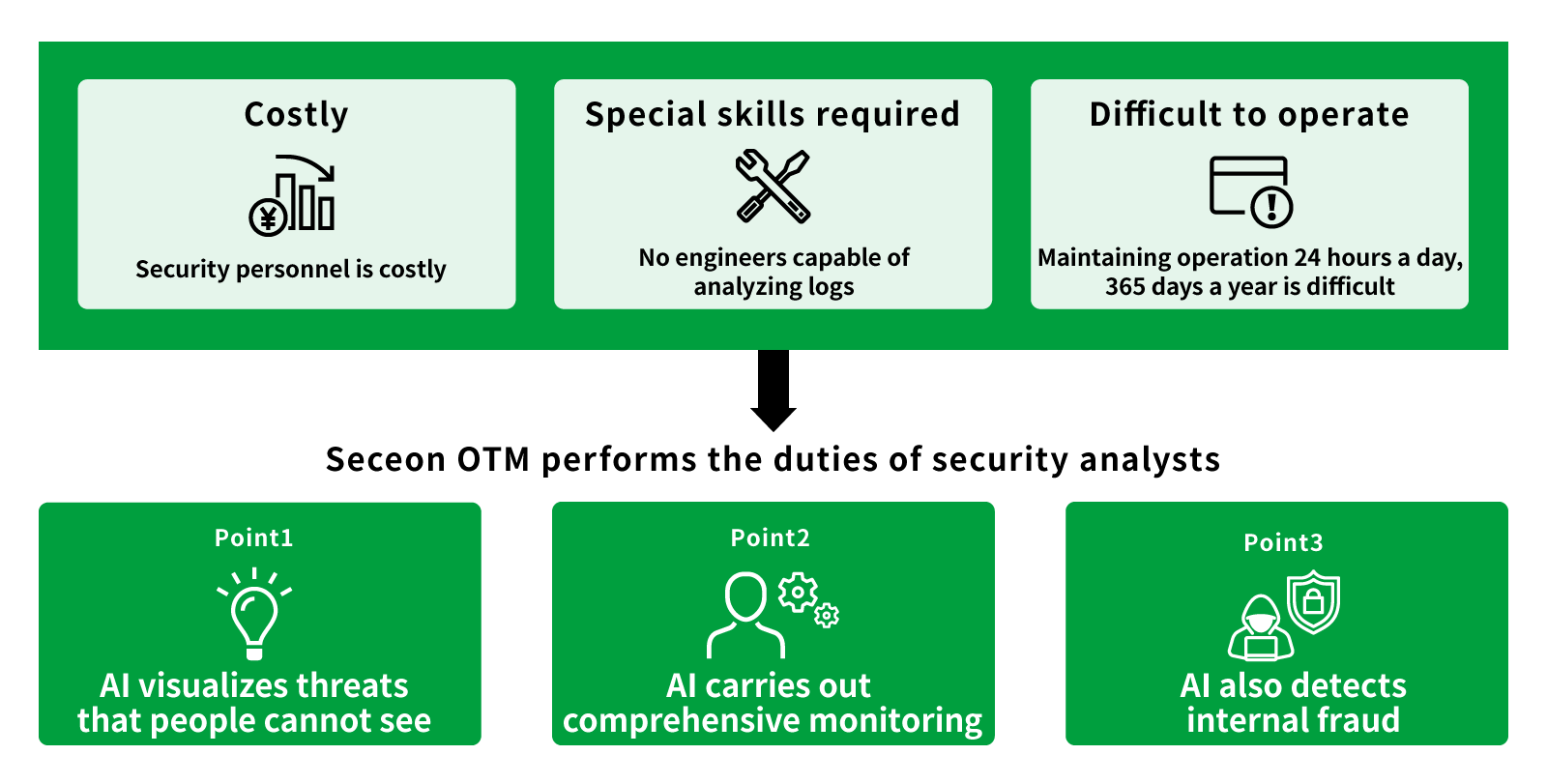
Seceon OTM is a security solution that uses AI machine learning. Through the visualization of data flowing in the network, the solution supports the handling of threats (information leakage due to malware activities, DDoS attacks, etc.) from detection to remediation.
The AI detects threats in real time through a completely new method combining behavioral and dynamic threat analysis. Additionally, by using Seceon OTM to automate SOC operations it is possible to significantly reduce the cost of security measures including SOC operation costs.
Even though the solution uses advanced technologies such as AI and machine learning, it requires no specialized knowledge/skills to operate, making it easy for customers to navigate.
Features
- Enables easy operation through basic knowledge of networks and security
- Data flowing through the network is collected, reducing network and server load
- In principle, tuning is unnecessary because the baseline is learned by machine learning
- Reduces operational costs through automatic policy checks using AI
- Knowledge of advanced security is not required since AI will perform the countermeasures
- AI performs correlation analysis of dangerous signs
- Easily achieves incident management
The service will help companies that:
- Want to reduce personnel costs, installation costs, and operating costs related to security
- Want to introduce advanced security that will resist sophisticated and complicated cyberattacks
- Want to easily introduce a powerful security system without making major changes to the current system
- Are not confident in their ability to independently operate a new, complex, multi-functional product
- Are unsure on what new security systems to introduce, but want to review existing measures
- Want to protect against internal fraud or leakage of information from inside the company
- Want to protect against targeted attacks which are increasing every year
- Want to prevent damage caused by ransomware
- Want to take comprehensive security measures for the various devices connected inside and outside the company
Main Functions
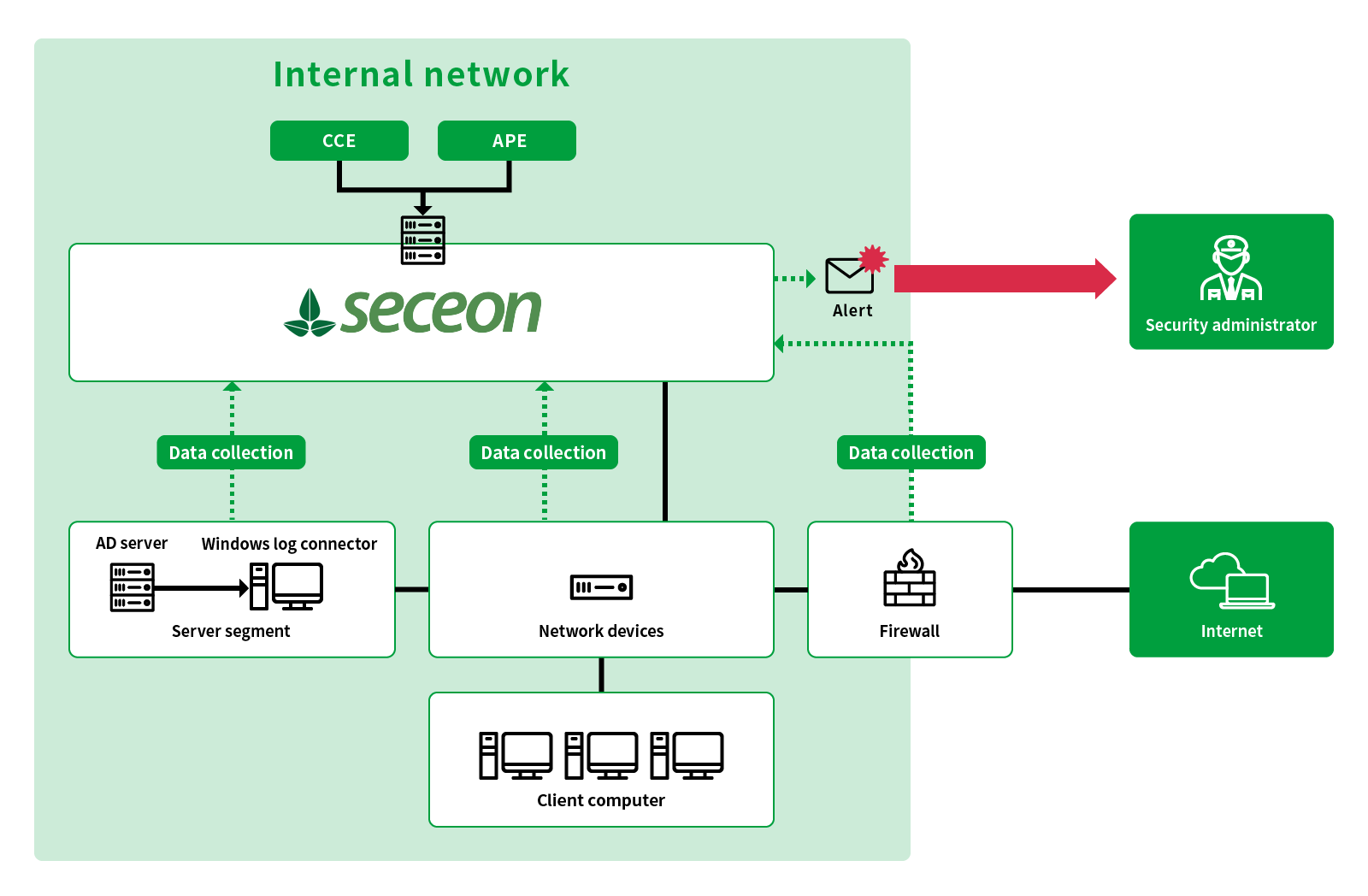
- Data collection
Collects the following data from the data flowing through the network and performs security analysis.
・Sender
・Recipient
・Data size
・Time stamp
Also collects system logs and AD logs to analyze user behavior. - Establishing Baseline
Uses machine learning to create a baseline; a standard for normal communication and behavior within the organization. - Threat indicator
Detects abnormalities by comparing the collected data with the baseline. If an abnormality is detected, an index is generated and accumulated as a threat indicator. - Correlation analysis and alert
Perform correlation analysis for the accumulated threat indicators and issue alerts only for real threats. AI analysis is characterized by fewer false detections than the manual work of security analysts. - Dashboard with simple design
Organizes and displays only the required information. This dashboard function avoids confusion even when an incident occurs and enables accurate understanding. - Easy-to-understand alert message
The list displays alerts from the highest urgency in the display format according to the three levels of risk, freeing the administrator the hassle of having to prioritize response. Recommended measures are also presented together with the alerts. - Flexible installation for any environment
Flexible installation is possible for any environment such as on premise or cloud. When introducing the solution at multiple sites, simply install an analysis server at the base and a data collection server at each site. It is not necessary to station an administrator at each of the sites.
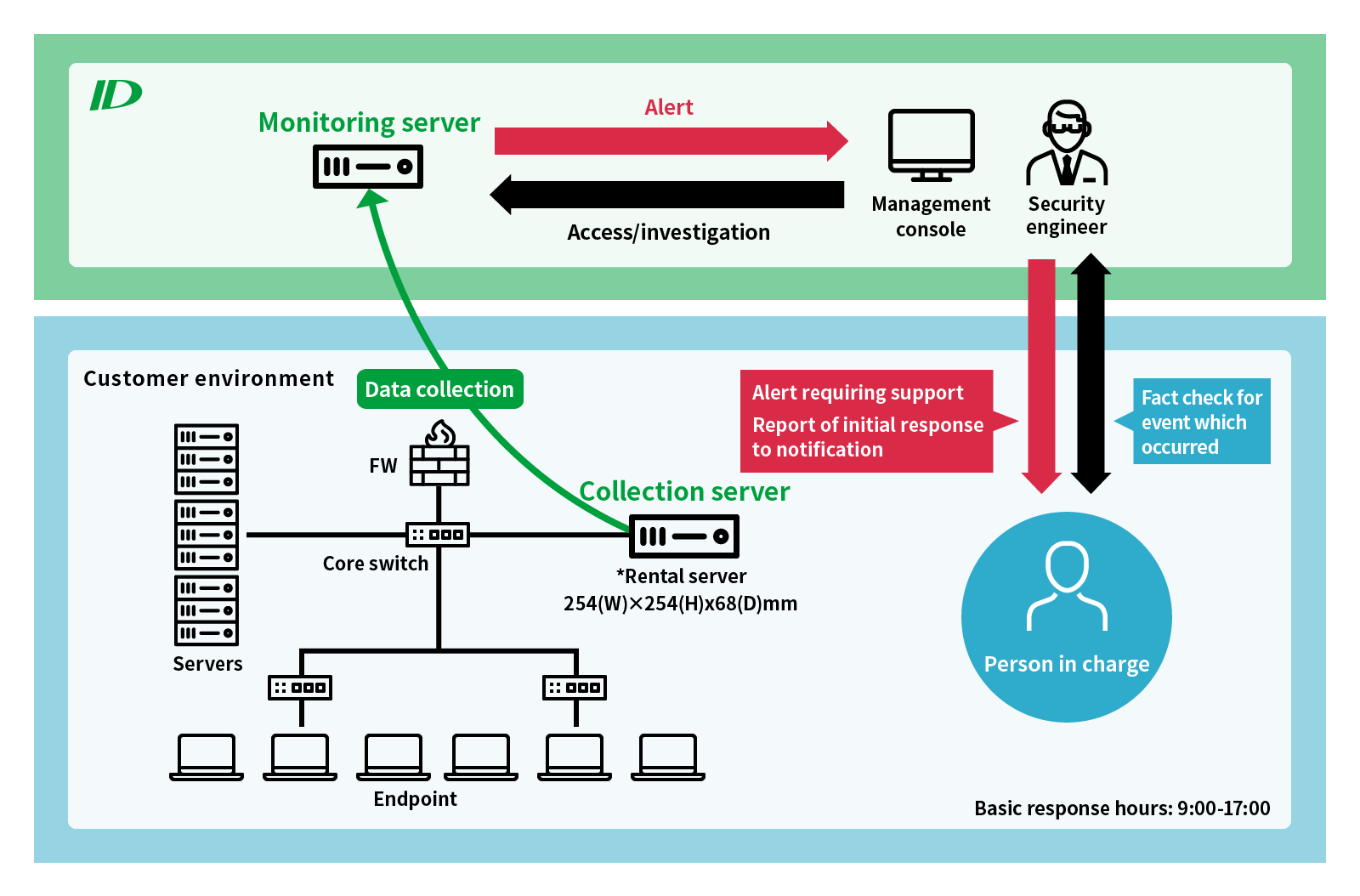
Network monitoring service using Seceon OTM
The ID Group also uses Seceon OTM to provide security monitoring services within the network on behalf of customers. The monitoring targets are all terminals in the network that have an IP address; for example, computers, mobile terminals, and IoT terminals.
Specifications
| Extra-Lite configuration | Lite configuration | Standard configuration | ||||
|---|---|---|---|---|---|---|
| APE+CCE | APE+CCE | APE+CCE | ||||
| CPU | Frequency | 2.0GHz | Frequency | 2.1GHz | Frequency | 2.1GHz |
| Core×Number of CPUs×Thread | 16 | Core×Number of CPUs×Thread | 32 | Core×Number of CPUs×Thread | 64 | |
| Memory | 64GB | 128GB | 196GB | |||
| Disk | 1TB SSD | 3TB SSD | 6TB SSD | |||
| *SSD is recommended | *A minimum capacity of 480GB is required for the boot device. | *RAID 5 is recommended | *RAID 5 is recommended | |||
| NIC | 1GigE | 1GigE | 1GigE | |||
| Number of hosts | 300 | 500 | 2000 | |||
| Number of critical devices *1 | Up to 50 devices | Up to 300 devices | Up to 800 devices | |||
| IP address | 1×IPv4 routing is possible Internal IP address | |||||
| Extra-Large configuration | Split configuration | Windows Collector | ||||
| APE+CCE | CCE | |||||
| CPU | Frequency | 2.1GHz | Frequency | 2GHz | Frequency | 2GHz or higher |
| Core×Number of CPUs×Thread | 88 | Core×Number of CPUs×Thread | 4 | Core×Number of CPUs×Thread | - | |
| Memory | 384GB | 42GB | 2GB or higher | |||
| Disk | 9TB SSD | 150GB or higher | 40GB or higher | |||
| *SSD is recommended | *RAID 5 is recommended | |||||
| NIC | 1GigE | 1GigE | 1GigE | |||
| Number of hosts | 4000 | - | - | |||
| Number of critical devices *1 | Up to 1500 devices | - | - | |||
| IP address | 1×IPv4 routing is possible Internal IP address | OS:Windows 2012 Server | ||||
*1 A critical device is a device that outputs logs, data flowing through networks, etc.
Example: A server hosting a router, firewall, switch, or general services (IPS/IDS, HTTP, HTTPS, database, etc.)
■ Installation in BIOS mode is recommended
Example of Introduction
Example of software development/system operation management company
Location: Tokyo
Number of users: approx. 1,000
Concerns that can be addressed
- Although we have introduced computers, mobile terminals, and IoT devices, we are unsure whether current security management is sufficient
- We have received instructions from top management on to provide measures to regulate “internal fraud”
- We do not have a sufficient budget to establish a dedicated security team
- Currently, information system members handle security measures while simultaneously handling other duties, making them very busy and creating the risk that a security-related measure is overlooked
- We want to establish effective security measures without spending a lot of money
Introduction schedule of ID Group
| 1Week | Design |
|
|
| 2Day | Introduction |
|
|
| 8Days | Start of operation |
|
|
| 1Day | Transfer of operations (training) |
|
|
| Start of operation |
|
Operation system
ID (cooperation with customers)
- Irregular confirmation of production environment operation: Confirmation of infrastructure (container, Docker operation), collection status, etc.
- Provision of version upgrade information and implementation of upgrade
- Provide technical information (issues, bugs, release schedule, etc.)
Customer (cooperation between information system department and operation department)
Information system department: Alert reaction
- Confirm alert details
- Reference report
- Implement license
Operation department
- Daily inspection: Confirmation of daily reports
- Escalation at the time of receiving system alert